End-to-end encryption is the most secure way to communicate privately and securely online. By encrypting messages at both ends of a conversation, end-to-end encryption prevents anyone in the middle from reading private communications.
Microsoft has implemented Message Encryption in Office 365 that protects and controls sensitive emails. These enhancements are aimed squarely at helping by safeguarding sensitive email communications without hampering the ability of users to be productive inside or outside of their organization.
A couple months ago I have written an article in my blog about Message Encryption with Office 365. However, in this article I want to focus more about end-to-end encryption in general.
How does end-to-end encryption work?
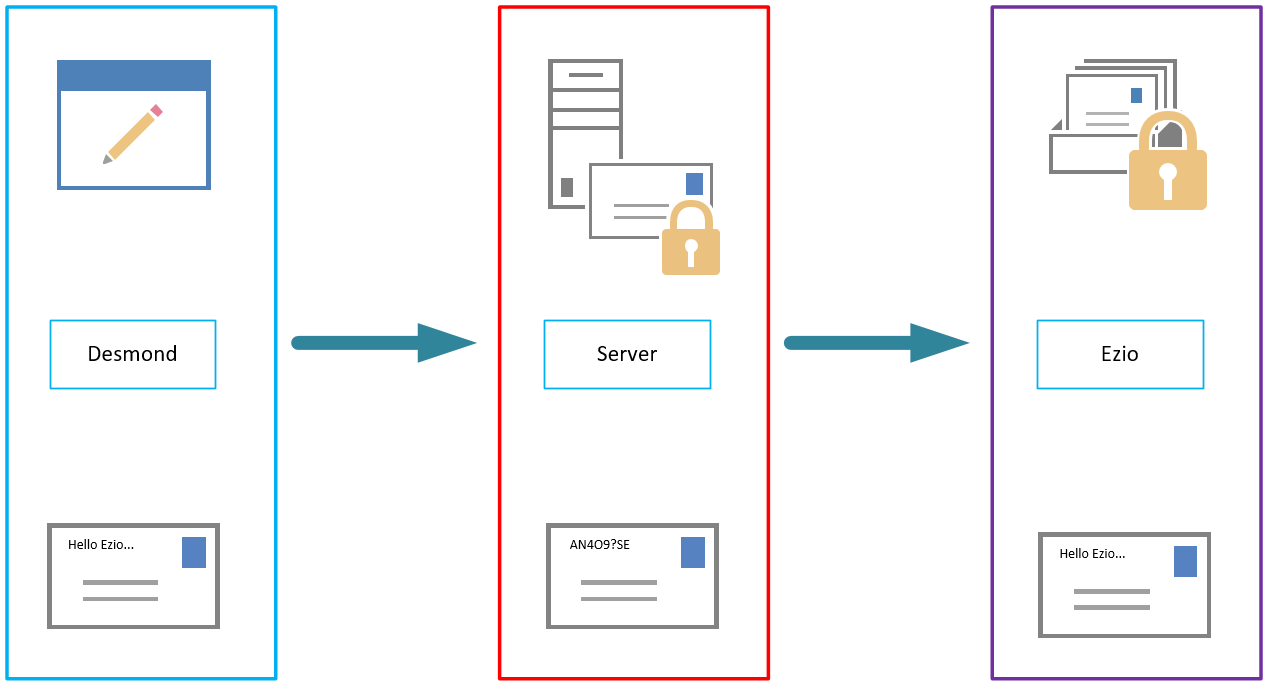
To understand how end-to-end encryption (E2EE) works, it helps to look at the picture below, In this example Desmond wants to send a private message to Ezio. Ezio has a public key and a private key. This key could look like the following example:


The public key can be shared with anyone, but only Ezio has the private key.
First, Desmond uses Ezio’s public key to encrypt the message, turning “Hello Ezio” into ciphertext – scrambled, seemingly random characters.

Desmond sends this encrypted message over the public internet. Along the way, it may pass through multiple servers, including those belonging to the email service they’re using and to their service providers. Although those companies may try to read the message, it is impossible for them to convert the ciphertext back into readable plaintext. Only Ezio can do that with his private key when it lands in his mailbox, as Ezio is the only person that has access to his private key. When Ezio wants to reply, he simply repeats the process, encrypting his message to Desmond using Desmond’s public key.
What are common email encryption scenarios?
There are a few scenarios we can go with, here 4 examples of them:
E2EE enterprise email encryption

Cloud based E2EE

E2EE with delivery to the public


