On October 31 Microsoft will disable TLS 1.1 for Exchange. If you have not changed your environment to TLS 1.2 yet, you should do that asap!
Here, the way how you can do this for Exchange server 2010 on Windows Server 2008 R2:
Disable SSL 3.0
The most steps we need to do are in the registry. Here we have some folders and entries which have to be created if they don’t exist yet. However, to disable SSL 3.0 on Exchange servers, we need to browse the registry to the following path:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\SSL 3.0
If this path does not exist completely, we can create it using PowerShell and the following command:
md "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0"
Now we need to create a new DWORD property, this can be done with the following command:
new-itemproperty -path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0" -name "Enabled" -value 0 -PropertyType "DWord"
Restart Server
At this point we need to reboot our server. This can be done with this PowerShell command:
Restart-Computer -ComputerName $computername -Force
Enable TLS 1.2
Now, we are ready to create the next keys in the registry to enable TLS 1.2 for client and server schannel communications. Note, they are not created by Windows out of the box.
This can be done by PowerShell as well. We simply run the following commands:
# Create keys in registry (not created by Windows out of the box) md "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2" md "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server" md "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client"
To enable TLS 1.2 we need this commands:
# Enable TLS 1.2 for client and server SCHANNEL communications new-itemproperty -path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server" -name "Enabled" -value 1 -PropertyType "DWord" new-itemproperty -path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server" -name "DisabledByDefault" -value 0 -PropertyType "DWord" new-itemproperty -path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client" -name "Enabled" -value 1 -PropertyType "DWord" new-itemproperty -path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client" -name "DisabledByDefault" -value 0 -PropertyType "DWord"
Edit the server to use of the 256-bit ciphers as default
Click Start->gpedit.msc
Expand Computer Configuration -> Administrative Templates -> Network and select “SSL Configuration Settings”
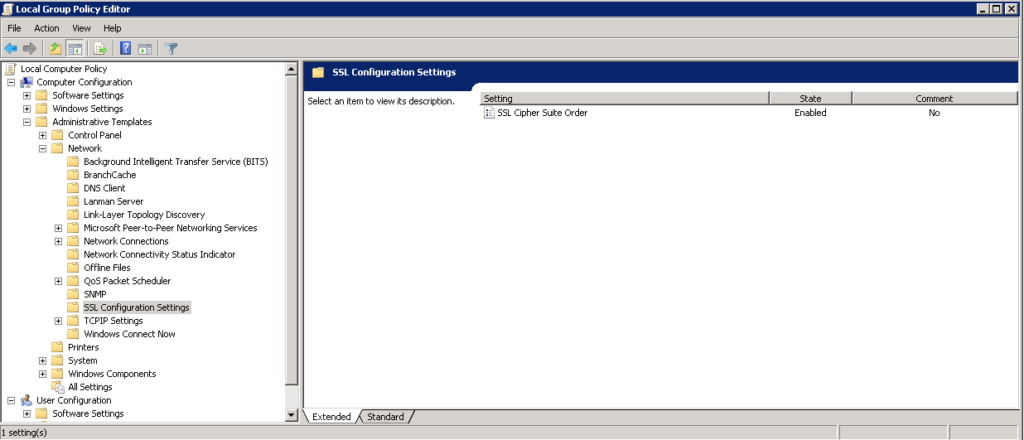
Double click “SSL Cipher Suite Order” and check “Enabled”
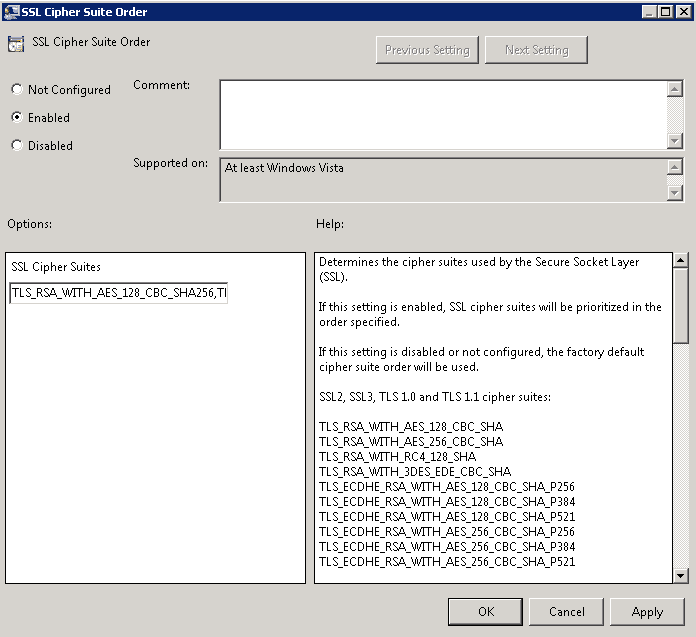
Copy the text from the “SSL Cipher Suites” and paste it into Notepad.
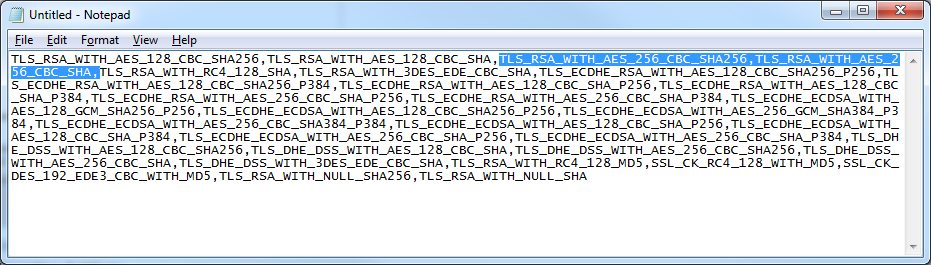
Move the following to the beginning of the text document: TLS_RSA_WITH_AES_256_CBC_SHA256,TLS_RSA_WITH_AES_256_CBC_SHA (Note: here you could remove lower strength ciphers from the order to prevent the server from accepting those connections).
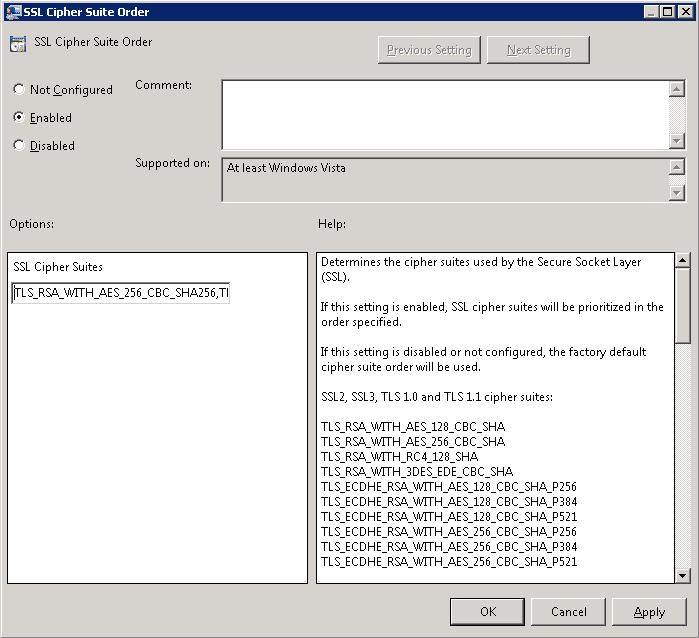
Paste the Cipher Suites back into the SSL Cipher Suites box in Group Policy and click OK
Restart the server for the changes to take effect.
Now, the Exchange server is ready for working with TLS 1.2.
Note: if you have load balancers, please enable TLS 1.2 and disabling TLS 1.0 and TLS 1.1 on the load balancers, too.
Photo by Patryk Grądys on Unsplash

