Working in IT shows us that one of the main things we must think about is to defend our organization from several types of cyber attacks.
In this and next two articles I am writing about what we must think to stay successful out there in the world wide web.
When we talk about preventing attackers form getting into our organization, we need to start from the most used attack point which is also from the attacker’s point of view, the most successful one – E-Mail.
Email is the primary attack vector for hacking and fraud, and the situation is only getting worse. From 2017 to 2018, email-based attacks on businesses increased 476%, according to the most recent threat survey by the cybersecurity firm Proofpoint. If we have a look on the statistics, we can see, that there are around 14’000 successfully scams by E-Mail worldwide that costs companies around 10 billion Euros.
However, this are only numbers that have been publicly published. I personally think that the dark figure still must be much higher.
How is that possible, that attacks by E-Mail are so popular?
Well, E-Mail is an easy way to get fast information about the company they attack. If we think of our own mailbox, we have to admit that we have certain information in our mailbox, which should not necessarily be where they are. These can be floor plans, credit card information, organizational charts, or other sensitive information that is sensitive to your organization.
Another point is, that depending on the role in the company, we are receiving a lot of emails every day. Or, depends on the size of the company, we do not always know all the employees.
Another point is, your email account is used to verify your identity, email addresses are often usernames, and a successful account takeover is an entry point to further attacks.
All these and other points make e-mail attacks so attractive and that’s why secure email practices must be a priority for your organization.
Most common attacks
In this capture we will have a look on the most common attacks out there in the internet. Please note, these examples are not the only once out there.
Fraud
There are different types of scam Mails out there. However, for this article we will divide them in three types:
“Regular” scamming: This are the emails, which for sure every one of us have received. These are emails from strangers hoping to send you millions of euros, Gold, etc., provided you cover their wire fees up front. Businesses are often the target of more sophisticated scams that use social engineering.
“Blackmail Emails”: This kind of messages are already a bit more sophisticated. The attacker usually uses your own email address as “proof” that he has gained access to your computer and caught you on something, mostly on the alleged visit of adult sites, and has fooled you. Now they try to blackmail you and to make you transfer a sum of bitcoins to an account. If you do not do this, he will add the footage to your contact list.
Most of the time, these scammers put more pressure on them by claiming that by clicking on this message, a countdown has been triggered and you only have 5 days to complete the transaction.
Especially by the trick with fake e-mail address and the fact that the users are insecure in such a message and are fearing an image loss, such news have unfortunately far too often success. Exact numbers I do not know, but since in this case the shame plays an important role, the dark number is very high.
“Business fraud”: This variant is very common in the business field, it is often like in “blackmail variant”, the attacker fakes the sender email address. The attacker usually sends messages as a leader from your own company with the instruction to do something.
In most of the cases, you should initiate a payment or reset his password to the one he has mention in the mail, etc.
These attacks can be random and easy to figure out as them, for example I am working in a swiss company and if I get an email from my boss in English to initiate a payment, I know it is be a fake.
However, caution is advised here, these attacks can also be very specific to the company. An example got a few years ago in Italy. In the process, an employee of an Italian Football Club from the Serie-A, who worked in Finance, was asked to trigger a payment which had to do with a real transfer. The attacker has written in this mail that there is still a fee for this transfer and this should be transferred to an appropriate account.
Phishing
Phishing attacks attempt to trick victims into clicking on links or downloading attachments in emails that appear to be legitimate. A lot of times, phishing emails are obviously fake. But sophisticated ones might spoof the “from” address to look like an official sender and design the email in a convincing way.
On what we have to pay attention, to identify, if a received E-Mail is a phishing email? Well, there are five main point we all should follow up:
Impersonal Salutation: Speeches like “Hello”, “andiheer” (the front part of my e-mail address), “Mr. / Mrs.” indicate a phishing e-mail. The attacker does not know your real name. This does not apply to targeted attacks.
You are not even a customer: If you receive mail with a call to action from a financial institution that you are not a customer to, it is a phishing email.
Suspicious attachments: Invoice or delivery confirmation as a Word document or an attached unsolicited application as a PDF: caution is advised in such cases. Especially if the filename is very generic (“facture.docx”). According Verizonlanden two-thirds of the malware infected via attachments on a computer. If in doubt, ask the (alleged) sender. But not by answering the mail. But by visiting the company’s website and looking for the contact information.
Spelling mistakes and simple language: Bad German or English and a simple language are features for phishing mail. This is, as mentioned in the beginning, but a question of the target group. Do not pull the converse conclusion that a correctly formulated mail is serious.
Specification of personal data: Will the sender want you to reply to the mail with personal information? That’s almost a guarantee for fraudulent mail, such as in the case of fictitious lottery winnings. Your bank, the provider or any other online service provider will never ask for your password. Such requests are another indication. It is more difficult if you are led to a login page. If in doubt, do not click on the link, but open the browser and type the address of the (alleged) sender there.
Let’s take a look at some phishing examples now:

In the first example it looks like we got an e-mail from PayPal and that there is a problem with our account. Our account is suspended, and we need to follow the Link to update our personal information and credential to unlock the account again.

In the second example we have clicked on an E-Mail with a Link, like the one from the first example with PayPal. In this example it looks like we need to login to our Facebook Account and the Website looks pretty like the real Facebook Website. However, if we have a closer look to the Web-address, we can see this is not the real Facebook Page. We see that there is a different Domain and no SSL Certificate which proves us that we are on Facebook.


In this example we got a (phishing) E-Mail with the information, that we have quit our Netflix membership. The Message looks real and it even shows a Support phone Number in the bottom. If you do have Netflix but you did not quit, you could get confused. So, the first thing in your mind could be that you want to “restart the membership” and you hit the Button to enter your credentials.
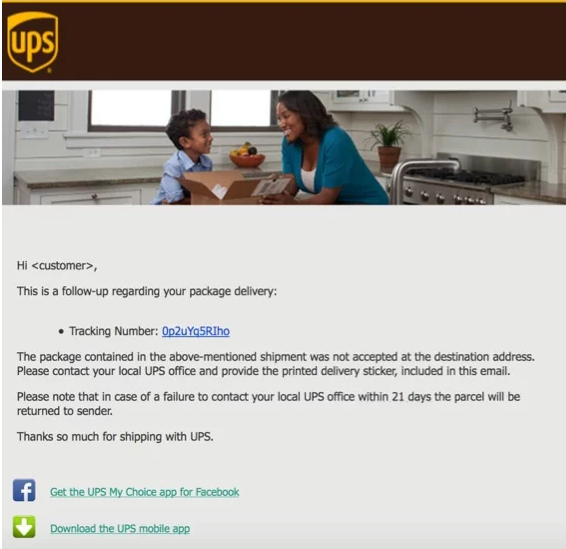
This example unfortunately is very common as well. You get a message from UPC (or any other company like UPC or DHL) with the message that you have missed the delivery. If you click on the tracking number your device will be immediately infected with malware.
What are the solutions?
Of course, there are technical aids to intercept such messages before they are delivered to users’ mailboxes. If we take Exchange Online Protection as an example, about 97% of such messages are already filtered out. At EOP, the messages are passed through several anti-virus and malware engines before they arrive at the user in the mailbox. You can find more information about EOP HERE.
What to do about the other 3 – 5 %? Well, there are some ways:
Train and test your employees
It’s important to create a culture of security awareness in your organization, and email security should be at the top of the list.
It is important to carry out training on these topics at regular basis.
These training sessions should happen soon after a new employee starts and then be updated periodically. The training should emphasize the most important aspects of the cyber security policy while also giving employees an understanding of the specific threats your management team has identified. These should be specific to your organization and to your industry. For example, if there are known threats targeting companies similar to yours through certain attack vectors, these training sessions are an excellent opportunity to educate your staff about preventing such attacks.
There are also third-party cyber security companies, that can help you there. Your cyber security officer should be tasked with researching and proposing a cost-benefit analysis for contracting outside security vendors.
Some teams or individuals may be more vulnerable to attack than others based on their specialty or level of access. Network administrators, managers, and anyone handling payroll or customer data may need additional training and attention.
In my company we carry phishing tests for some of our customers at irregular intervals. These can be generalized or sometimes very specific to the current situation in the customers company.
Here we test the behaviour of the end user whether they will be successfully completed, and if not, how they proceed with the fact of a phishing attack.
Require MFA
All employees in your organization who are using a company cloud account or have access to it by using the company credentials, should be multi factor authentication (MFA) enabled. If we have a look on Office 365, Microsoft provides us the possibility to enable this feature for all ore also some specific group of users. We even are able to choose between MFA by using SMS or an authentication App. For more information how to enable MFA in Office 365, I have written another article at my Blog which you can find HERE. As well you can find here on my Blog more information about the MFA functionality by using the Authenticator App by following the Link HERE.
Encrypted (and signed) E-Mails
If you are using an email service that does not use end-to-end encryption, then there is a possibility that a data breach will expose your organization’s emails. For certain organizations, this can also increase your liability for penalties under HIPAA and the GDPR.
If we use Exchange online with our Office 365 Tenant, we also can use Office 365 Message Encryption (OME).
Office 365 Message Encryption is offered as part of Office 365 Enterprise E3 and E5, Microsoft Enterprise E3 and E5, Microsoft 365 Business, Office 365 A1, A3, and A5, and Office 365 Government G3 and G5. Customers do not need additional licenses to receive the new protection capabilities powered by Azure Information Protection.
With Office 365 Message Encryption, your organization can send and receive encrypted email messages between people inside and outside your organization. Office 365 Message Encryption works with Outlook.com, Yahoo!, Gmail, and other email services. Email message encryption helps ensure that only intended recipients can view message content.
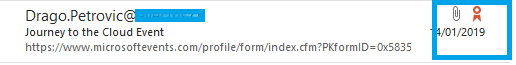
If you don’t want to or cannot encrypt messages, you still should “sign” it. Message signing can be done by using S/MIME certificates or PGP. This is a prove that the sender really is the sender and the message was not interrupted from an attacker. The end-user can see a small red ribbon at the received message. This ribbon will be show like this example:
For more information about S/MIME I can advice you the Link HERE at my Blog.
Mail Address Policies / Publishing Mail addresses
Every email address is an opportunity for an attacker. So, if you reduce the number of employees with publicly available email addresses, you can reduce your potential attacker’s options. You should only list essential employee names and contacts on your organization’s website. You can also consider using non-obvious email formulations that are difficult to guess. For example, instead of [email protected], you could use [email protected].
If you are publishing non-personal email addresses like [email protected] or [email protected] you need to make sure, that ONLY well-trained employees have access to this Mailboxes. These employees must have a sense of the risks they are exposed to.
Conclusion
As mentioned at the beginning of this article, this is the first of 3 articles on attack prevention. I decided to start with this topic because in my opinion it is the most critical of them all. There are a lot of Internet threads, most of them we can intercept technically, for those who get through to our end-users, it is important that our co-workers are well trained. This helps the company as well as each individually.

