Depending on the tenant configuration, there may be problems with the rollout of Team Certified phones.
Here is a solution:
Teams Certified phones can be rolled out in different ways. These rollouts generally work very well. If not, however, troubleshooting can become a considerable challenge.
When a company plans a rollout, there are several points that need to be considered in preparation. These points are very well described in the following Technet article.
From time to time, however, problems can occur with a tenant regardless of the rollout method used.
In the case I describe in this article, we tried the following two variants:
Normal rollout:
The device was connected to the network and the user tried to register on the new phone together with the device authentication. The registration failed with the following message:

The message on the picture is in German, but translated into English the error message means the following:
Logout in progress…
Registration in Intune has failed. Try again or contact your administrator.
When we look at the Teams Admin Center, the device is displayed after several attempts, but we also see that no user is logged on.

Even with our second variant of registering the device with a user via the Teams Admin Center, this process is aborted.
What next? Registration via the MAC address was also unsuccessful, with the same result.
The solution
Most of the time, the solution is just a click away. After also checking the sign-in logs, we could not identify the error.
Teams Devices are added to a tenant through the Intune registration process, but are subsequently deposited and managed in the Teams Admin Center.
In our case, it was still an Intune configuration that we had to adjust in order to find the solution.
The following steps then led us to the desired solution:
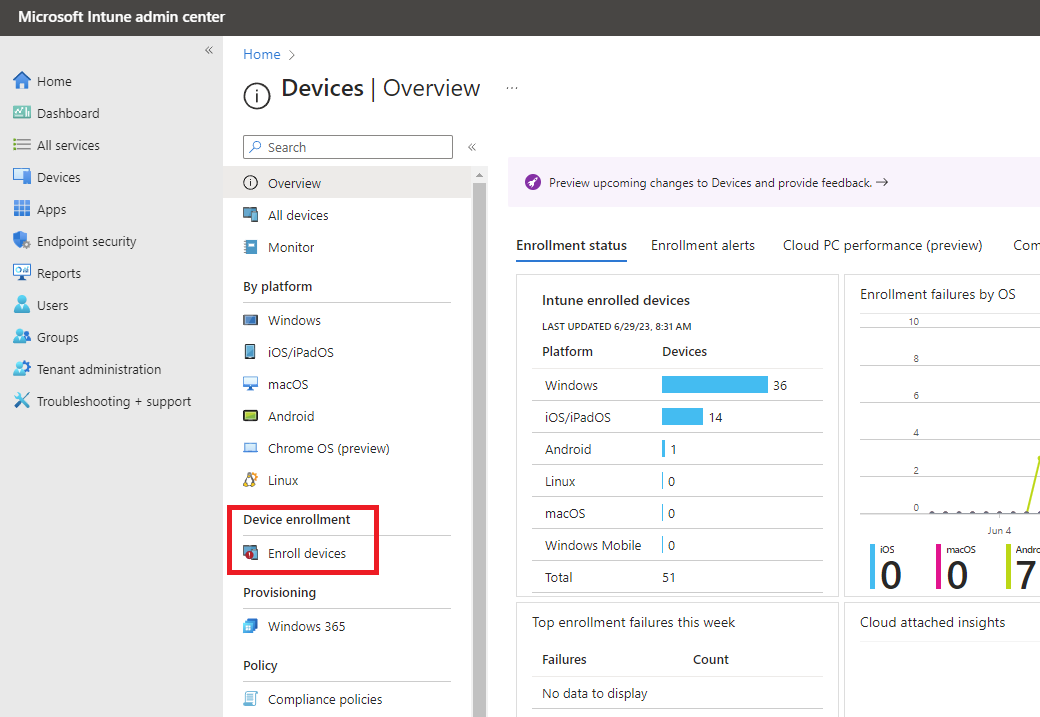 |
In the Intune Admin Center, browse to Devices > Enroll devices. |
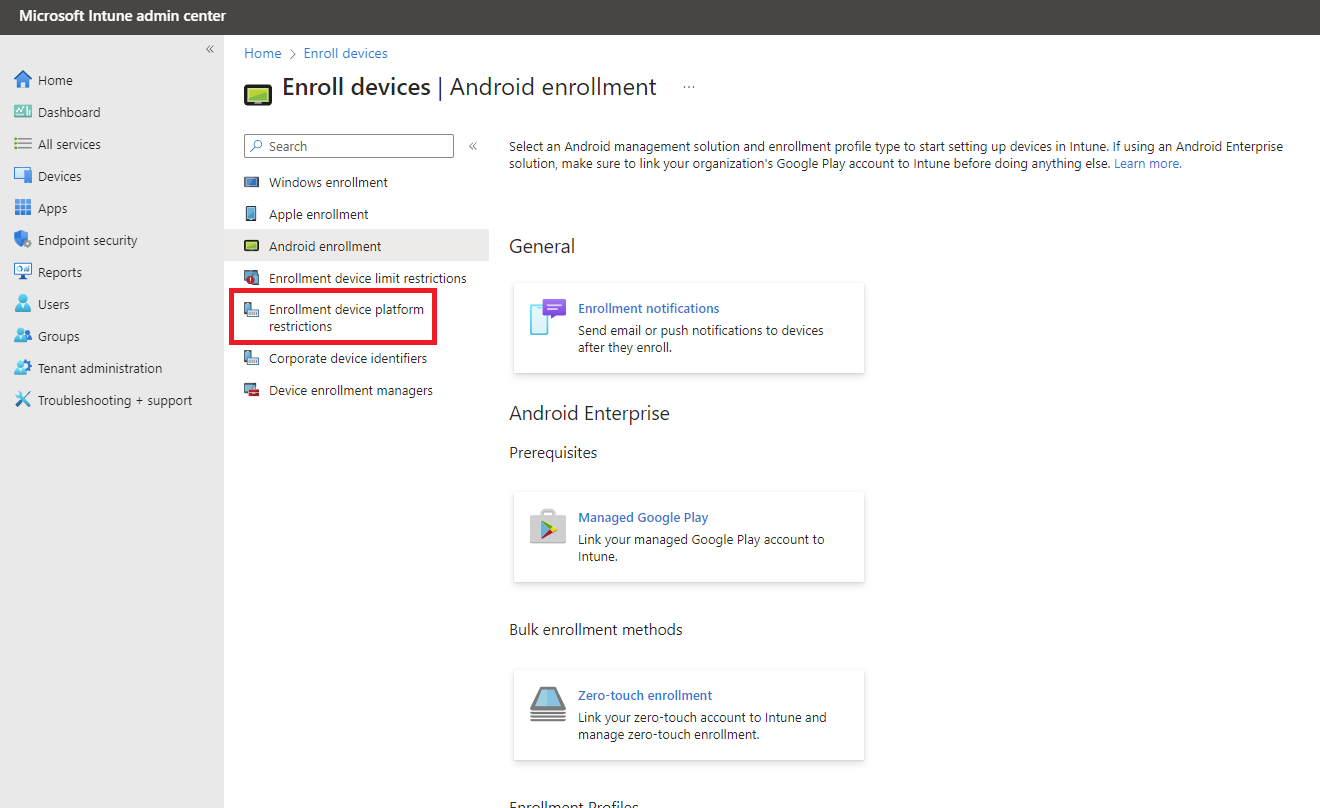 |
Go to Enrollment device platform restrictions |
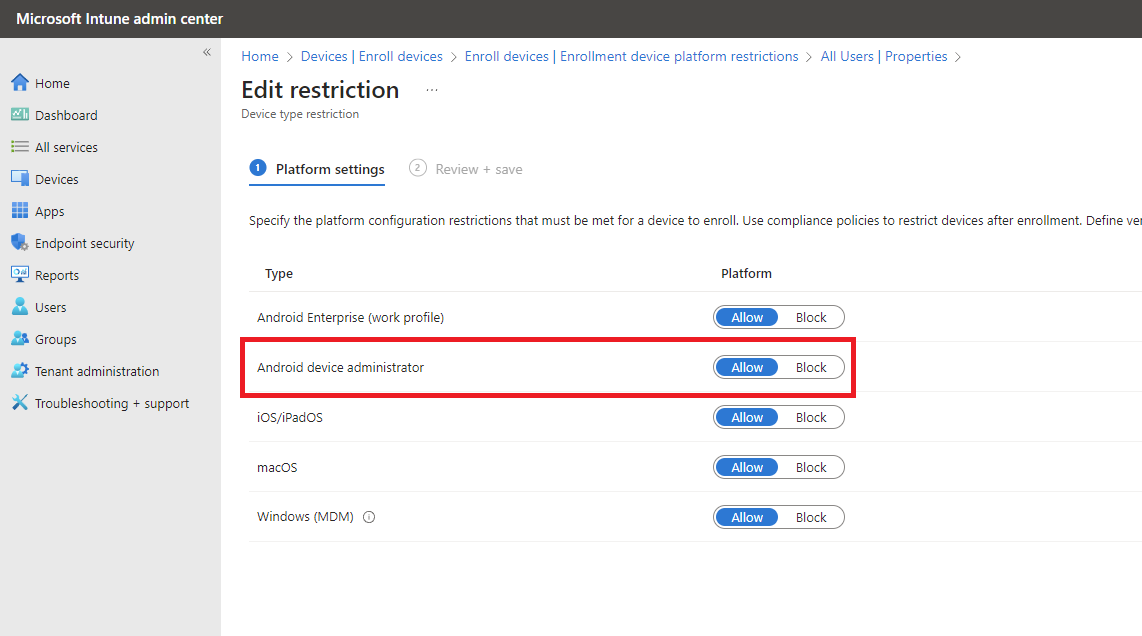 |
In our specific case, the Android devices administrator option was set to Block. We changed this setting to Allow. |
After adjusting this setting, we restarted the onboarding process…. This time with success:

Additional Points
During this troubleshooting process, we became aware of several factors. When troubleshooting, please ensure that the devices do not get stuck with a conditional access policy.
One approach to solving this problem can be the following:
Create a dynamic Azure Active Directory group that is tailored to your hardware. As an example at Yealink:
Dynamic membership rules: (device.devicePhysicalIds -contains “Yealink”) or (device.deviceManufacturer -contains “Yealink”) or (device.displayName -contains “Yealink”).
This Dynamic Group can then be added to the Conditional Access Rules as an “Exclude”. This way we make sure that this does not cause any problems.
This is only a variant and is applicable depending on the security directives of the respective companies.